Reverse Engineering an American Express USB WebKey May 26, 2015
I received a strange piece of hardware in the mail the other day. American Express is piggy-backing on LegalZoom document deliveries with an interesting piece of marketing – a USB key-like device in the shape of a credit card.

Thinking it was a USB drive and one that I might be able to format and reuse for something else, I plugged it in to my Mac. To my surprise, it immediately opened Safari and a website pointing to an American Express credit card offer. Huh? I thought OS X didn’t have Autorun support. So, of course, I tried it again. This time, I noticed that the address bar in Safari scrolled as if someone was typing really fast.
Holy trickery, Batman. It’s mimicking a USB keyboard!
Here are the steps that it takes:
- ⌃F3 to focus the Dock
- Types:
Safari - return to launch Safari
- ⌘L to focus the address bar
- Types:
http://www262.americanexpress.com/landing-page/business-cards/sclp/bgold/aff0022/44460?PID=15&BUID=SBS&PSKU=BGR&CRTV=LZBGRLTOWBKYREF15 - return to launch site
NOTE: If Safari isn’t running or pinned to your Dock, the entire process fails. They probably would have been better served to start with ⌘-space and a Spotlight search instead.
Digging In
My curiosity was piqued, and this reminded me of the USBdriveby project that Samy Kamkar discussed on a recent Tim Ferriss podcast.
I wondered if I could reprogram this American Express USB device to behave in a similar way as the Teensy USB Microcontroller that Samy used.
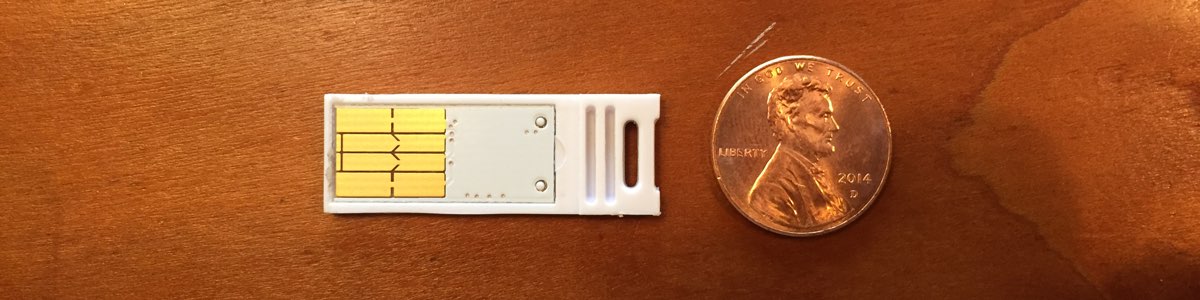

Find the USB Device
First, let’s see what OS X thinks about this USB device. We’ll do that by inspecting all USB devices both before and after plugging in the USB key. The difference will help us find the device itself.
system_profiler SPUSBDataType > ~/usbout.txt
system_profiler SPUSBDataType > ~/usbin.txt
diff ~/usbout.txt ~/usbin.txt
This should yield a result like the following:
33a34,44
> WEBKEY:
>
> Product ID: 0x6662
> Vendor ID: 0x05ac (Apple Inc.)
> Version: 8.15
> Speed: Up to 12 Mb/sec
> Manufacturer: TP6662
> Location ID: 0x14500000 / 27
> Current Available (mA): 500
> Current Required (mA): 100
Note the Product ID and Vendor ID values. We’ll need those later.
I find it fairly suspicious that it mimics hardware from “Apple Inc.” Kinda sketchy.
Now What?
At this point, I was immediately stuck, but after some research, I found a superuser question on Stack Exchange titled Can I “reprogram” an American Express USB drive? No direct answers, but this answer gave me hope:
It consists of a Cypress PSoC controller, combined with a 24c02 serial eeprom … With a simple program called PonyProg you can read and modify the contents of the eeprom. http://superuser.com/a/216810/8424
I spun my wheels for a long while with no luck, but later, I found an article titled Hacking USB Webkeys. This looked promising.
Hardware Surgery (and Failure)
I slowly pried the chip from it’s plastic enclosure. It was attached with some glue.

Sweet. Contact points that I should be able to use to access the EEPROM.
All seemed well, until I tested the webkey again. I must have damaged something, because it now skips every 5th to 8th character as it emulates a keyboard. Shoot. Maybe next time.
Let’s [Pretend to] Read all the EEPROM
Disclaimer: I wasn’t able to test any of this, because I damaged my hardware, but I encourage others to carry on where I left off and let me know if you have any success!
As it turns out, PonyProg (the program mentioned on the Stack Exchange post) doesn’t work on OS X, but I found a program called ch341eeprom that claimed to perform a similar task.
It depends on the WinChipHead CH341A.
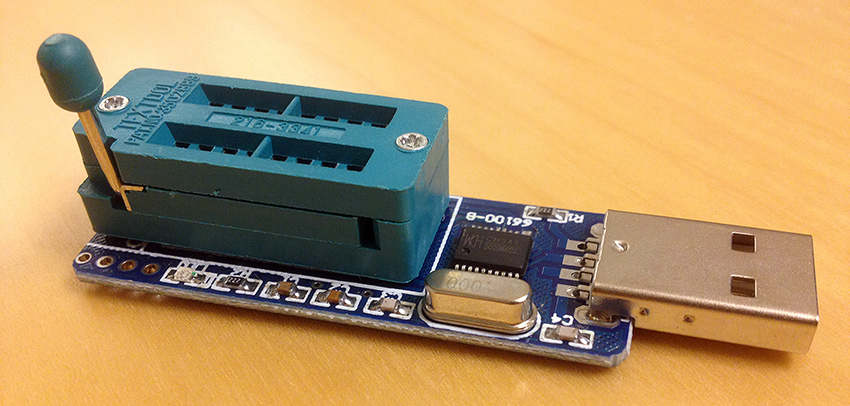
It also depends on libusb, so let’s install that using
Homebrew and then clone the repository so we can compile
ch341eeprom.
brew install libusb
git clone https://github.com/commandtab/ch341eeprom.git
cd ch341eeprom
Compile, and try to read the eeprom:
make
ch341eeprom -v -s 24c02 -r ~/eeprom.bin
Conclusion
While my attempt at hacking this hardware resulted in catastrophic failure, don’t let that stop you from trying something new or breaking down an unknown piece of tech. I learned a lot during this little investigative project, and if I find another free marketing webkey in the mail, I just might pick-up where I left off.
Please share, reply to comment, or retweet. Also follow me for more.
Tweet Follow @rmm5t